Note: This guide is a work in progress and will be updated as new information or functionality emerges, so bookmark it for future reference.
Last Updated: 2025/04/26 01:30 (Europe/Copenhagen)
Intro
GitHub Copilot is a powerful AI coding assistant for Visual Studio Code (VSCode), but its default settings can risk exposing sensitive data like API keys, tokens, or passwords. This guide details how to configure Copilot securely, prioritizing privacy to prevent data leaks. We’ll cover GitHub Privacy Settings, VSCode Privacy Settings – including telemetry and content exclusion, extension installation, authentication, and I’ll also clear the confusion around .copilotignore and explain why it has no practical effect in VSCode today.
Importance of a Privacy-First Setup
Improperly configured AI tools like Copilot may transmit sensitive code snippets to GitHub’s servers for processing or training. This guide minimizes data sharing, disables telemetry, and excludes sensitive files, ensuring Copilot enhances productivity without compromising proprietary or confidential data – a critical step for developers handling sensitive projects.
1. GitHub Privacy Settings
Navigate to GitHub Copilot settings and disable:
- Copilot can search the web
- Allow GitHub to use my data for product improvements
- Allow GitHub to use my data for AI model training
Disabling “Copilot can search the web” prevents Copilot from sending queries online, minimizing data exposure. While this might have a minor effect on bleeding-edge issues, it shouldn’t impact general coding or everyday use.
GitHub Copilots explanation:
Disabling web search means Copilot won’t supplement its suggestions with the latest information from the internet, which could reduce the freshness or breadth of its responses.Opting out of “Allow GitHub to use my data for product improvements” and “Allow GitHub to use my data for AI model training” ensures your code isn’t used to enhance GitHub’s models, safeguarding proprietary logic, and wont affect Copilot’s suggestion quality. Those settings just control how GitHub uses your data on the backend, not how Copilot works for you.
GitHub Copilots explanation:
Opting out of "Allow GitHub to use my data for product improvements" and "Allow GitHub to use my data for AI model training" ensures that your code and interactions are not used by GitHub to train or improve Copilot’s models. This helps safeguard your proprietary or sensitive logic.
These settings do not affect the quality of Copilot’s suggestions for you.
They only control whether your data is used to improve Copilot for everyone in the future, not how Copilot generates suggestions for you right now.The “Suggestions matching public code (duplication detection filter)” setting, whether allowed or blocked, allows snippets up to 150 characters to be sent to GitHub for comparison, risking transmission of sensitive data like API keys or tokens. While Copilot’s filters block sensitive information (e.g., credentials, emails) from suggestions, and Copilot Chat in VSCode discards prompts after responses, later steps in this guide will explain how to block Copilot from accessing sensitive config files and other sources entirely, preventing these snippets from being sent.
2. VSCode Privacy Settings
Before addressing GitHub Copilot directly, let’s start by locking down VSCode’s telemetry and data sharing.
We disable core telemetry, feedback prompts, experimental features, automatic extension updates, ignore extension recommendations, and finally extension-based telemetry. Then we focus on preventing Copilot from processing sensitive local files.
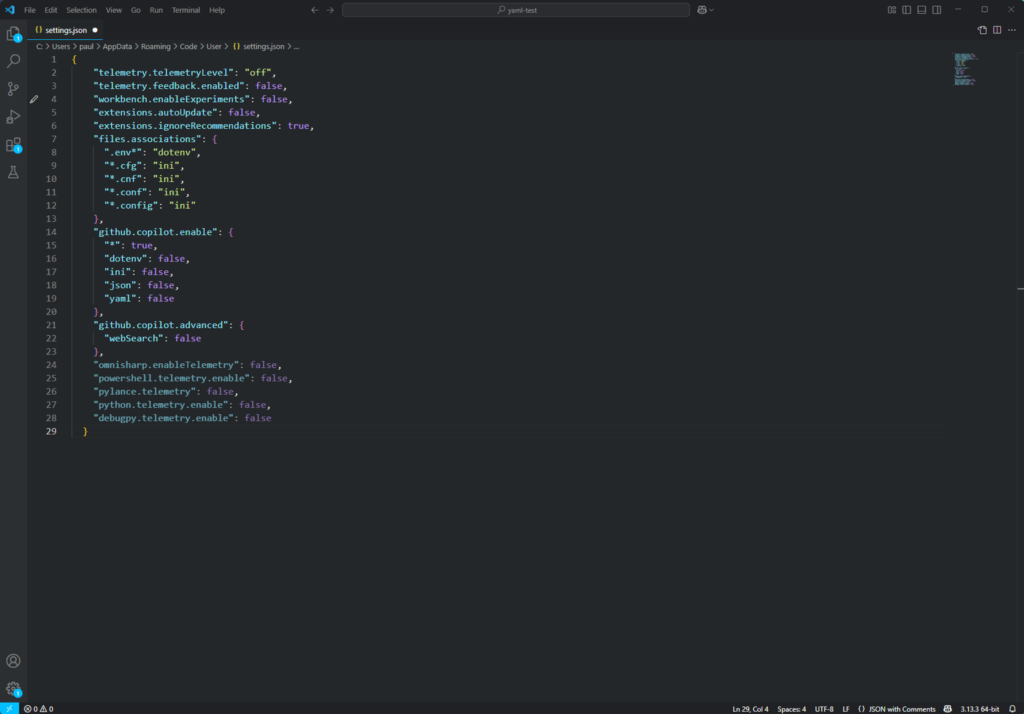
Start by pressing Ctrl+Shift+P in VSCode, select “Preferences: Open User Settings (JSON)”, and add the following to your settings:
{
"telemetry.telemetryLevel": "off",
"telemetry.feedback.enabled": false,
"workbench.enableExperiments": false,
"extensions.autoUpdate": false,
"extensions.ignoreRecommendations": true,
"files.associations": {
".env*": "dotenv",
"*.cfg": "ini",
"*.cnf": "ini",
"*.conf": "ini",
"*.config": "ini"
},
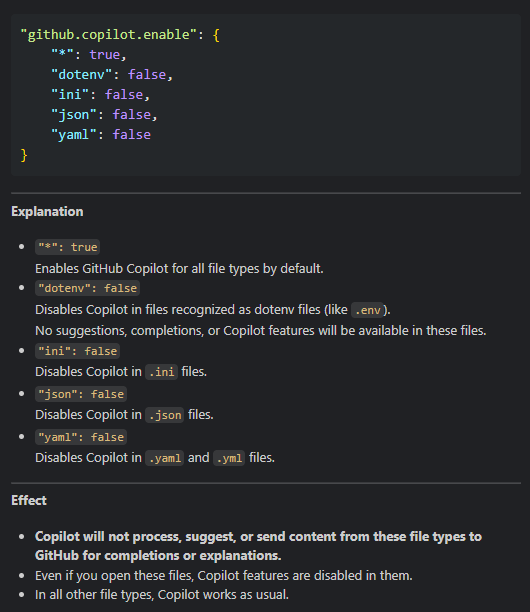
"github.copilot.enable": {
"*": true,
"dotenv": false,
"ini": false,
"json": false,
"yaml": false
},
"github.copilot.advanced": {
"webSearch": false
},
"omnisharp.enableTelemetry": false,
"powershell.telemetry.enable": false,
"pylance.telemetry": false,
"python.telemetry.enable": false,
"debugpy.telemetry.enable": false
}
Core Telemetry and Behavior Settings
telemetry.telemetryLevel: "off": Disables all core VSCode telemetry, preventing usage data, crash reports, and error data from being sent to Microsoft after activation.telemetry.feedback.enabled: false: Disables feedback prompts, avoiding data collection.workbench.enableExperiments: false: Prevents experimental features that may introduce telemetry.extensions.autoUpdate: false: Halts automatic extension updates, letting you vet changes.extensions.ignoreRecommendations: true: Stops automatic extension recommendations, which can involve data sharing.github.copilot.advanced.webSearch: false: Ensures Copilot’s web search is disabled in VSCode.
Extension Telemetry
Settings like omnisharp.enableTelemetry, powershell.telemetry.enable, pylance.telemetry, python.telemetry.enable, and debugpy.telemetry.enable disable telemetry for C#, PowerShell, and Python extensions, which may otherwise collect code snippets or usage data.
File Associations and Copilot Enable
To stop Copilot from processing, suggesting, or sending content from specific file types (such as .env, .ini, .json, .yaml, etc.), we use the github.copilot.enable setting to disable it for these selected file types – even if those files are opened in the editor.
Warning: If you open a blocked file type and click the Copilot icon in the bottom-right corner, then select “Code Completions (FileType)“, Copilot will permanently enable that file type in github.copilot.enable.
To disable it again, you must manually uncheck the option or edit your settings.json file.
For Copilot to correctly recognize and apply language types, to non-standard or custom-named file types, we use use files.associations. For example, .env.local is not recognized as a dotenv file by default, so this step ensures it is treated correctly and that Copilot respects the block.
File types like .cfg, .cnf, .conf, and .config are not associated with any specific language types either, so we manually assign them to ini, which we have blocked in our Copilot settings.
GitHub Copilots explanation:
3. Install Copilot Extensions
Open VSCode Extensions (Ctrl+Shift+X), search for “GitHub Copilot” and install it. It will automatically install “GitHub Copilot Chat” as well. Both are official extensions by GitHub. The Copilot extension handles code completion, while Copilot Chat supports conversational queries. Official extensions ensure compatibility, and our privacy settings limit their data-sharing risks.
4. Authenticate with GitHub
When prompted in VSCode, sign in to your GitHub account to activate Copilot.
This links the extension to your account, enabling features within usage limits of your plan.
If you have never set up Copilot before, you’ll start with a free plan.
The confusion about .copilotignore
There seems to stem a lot of confusion about .copilotignore, and with good reason. It took me a lot of time and digging to get to the bottom of its functionality – or more precisely, lack thereof. After intensive digging I can conclude that .copilotignore has no practical effect in VSCode today.
What Copilot Claims It Does
According to Copilot Chat and common assumptions in the community, .copilotignore is meant to work similarly to .gitignore:
- It should exclude specified files and folders from Copilot’s suggestion context in other files.
In theory, this would help prevent secrets or irrelevant content from influencing completions, especially from files like .env, .json or.yaml.
What Actually Happens
Through extensive testing, the reality is very different:
- If a file has never been opened in the current VSCode session, Copilot will not use it for suggestions – regardless of whether it’s listed in
.copilotignore. - If the file has been opened once, Copilot will freely use its contents in suggestions even if it is explicitly listed in
.copilotignore.
This means Copilot’s behavior is entirely dependent on open/recent file state, and not at all on the contents of .copilotignore.
Confirmed by Copilot Itself
In a direct Copilot chat session, it confirmed:
.copilotignore has limited practical effect in today’s Copilot for VS Code, because Copilot only uses open/recent files for context. Its intended purpose is to filter background context, but in reality, it rarely changes Copilot’s behavior unless Copilot’s context model expands in the future.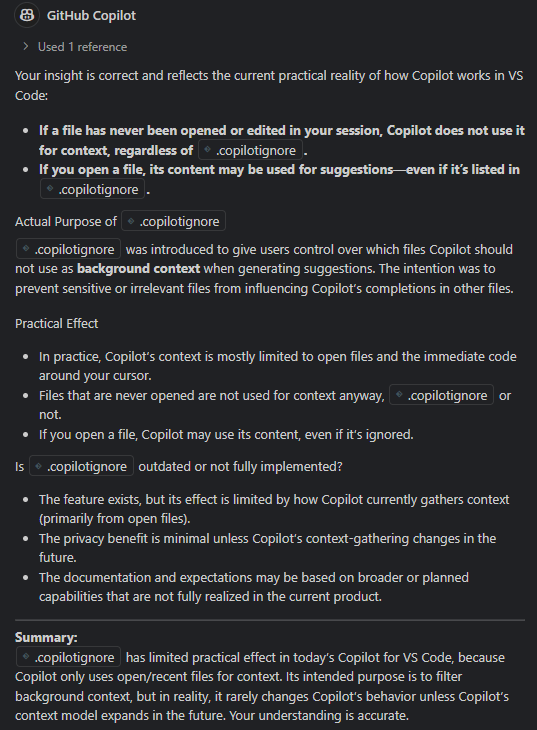
Verdict
It strongly suggests that .copilotignore is either left-over functionality, never fully implemented, or perhaps quietly deprecated – yet still referenced by Copilot’s own suggestions.
Until Copilot’s context engine changes or official clarification is provided, .copilotignore should not be relied on as a functional privacy or filtering tool in VSCode.
Conclusion
We’ve secured GitHub Copilot in VSCode by disabling GitHub’s data-sharing options, tightening VSCode telemetry and Copilot settings, preventing Copilot from processing data in sensitive files, installing official extensions, and authenticating safely. This setup ensures Copilot aids coding without risking sensitive data exposure.
Stay cautious: monitor GitHub and VSCode updates for changes to telemetry defaults, and keep your file exclusion settings up to date. For Copilot Business or Enterprise users, check organization-level content exclusion policies. This approach balances AI productivity with robust privacy.